This project is born with the aim to develop a lightweight, but useful tool. The reason is that the existing hex editors have some different limitations (e.g. too many dependencies, missing hex coloring features, etc.).
This project is based on qhexedit2, capstone and keystone engines. New features could be added in the future, PRs are welcomed.
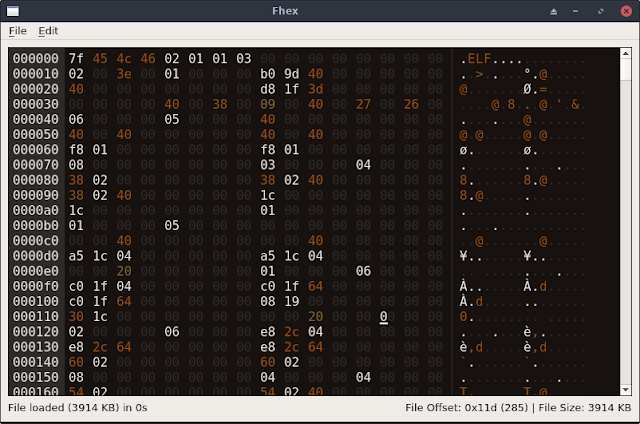
Features- Chunks loader - Used to load only a portion of large files without exhaust the memory (use alt + left/right arrows to move among chunks). Please note that in chunk mode, all the operations (e.g. search) applies only to the current chunk except for file save (the entire file is saved). However, each time you edit a chunk, save it before to move to another chunk, otherwise you will lose your changes.
- Search and replace (UTF-8, HEX, regex, reverse search supported) [
CTRL + F] - Colored output (white spaces, ASCII characters, 0xFF, UTF-8 and NULL bytes have different colors)
- Interpret selected bytes as integer, long, unsigned long [
CTRL + B] - Copy & Paste [
CTRL + CandCTRL + V] - Copy selected unicode characters [
CTRL + Space] - Zeroing all the selected bytes [
DeleteorCTRL + D] - Undo & Redo [
CTRL + ZandCTRL + Y] - Drag & Drop (Hint: Drag&Drop two files to diff them)
- Overwrite the same file or create a new one [
CTRL + S] - Goto offset [
CTRL + G] - Insert mode supported in order to insert new bytes instead to overwrite the existing one [
INS] - Create new instances [
CTRL + N] - Basic text viewer for the selected text [
CTRL + T] - Reload the current file [
F5] - Compare two different files at byte level
- Browsable Binary Chart (see later for details) [
F1] - Hex - Dec number converter [
F2] - Hex String escaper (e.g from 010203 to \x01\x02\x03) [
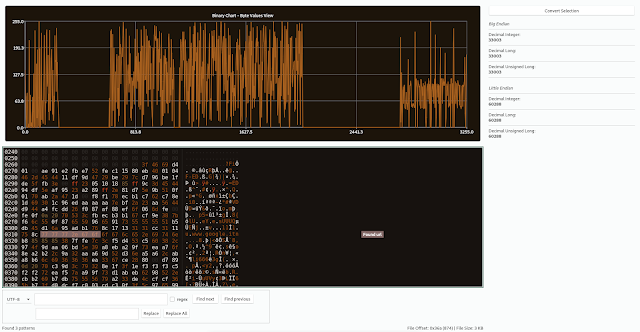
F3] - Pattern Matching Engine (see later for details)
- Disassebler based on Capstone Engine [
F4] - Assembler based on Keystone Engine [
F4] - Zoom-Out/Zoom-In bytes view (
CTRL + Up/DownorCTRL + -/+) - Shortcuts for all these features
Fhex can load at startup a configuration file (from ~/fhex/config.json) in JSON format with a list of strings or bytes to highlight and a comment/label to add close to the matches.
Examples:
{
"PatternMatching":
[
{
"string" : "://www.",
"color" : "rgba(250,200,200,50)",
"message" : "Found url"
},
{
"bytes" : "414243",
"color" : "rgba(250,200,200,50)",
"message" : "Found ABC"
}
]
}To activate pattern matching press CTRL + P At the end, Fhex will show also an offset list with all the result references. Note: Labels with comments are added only if the window is maximized, if labels are not displayed correctly please try to run pattern matching again.
Fhex has the feature to chart the loaded binary file (Note: In order to compile the project, now you need also qt5-charts installed on the system). The y-axis range is between 0 and 255 (in hex 0x0 and 0xff, i.e. the byte values). The x-axis range is between 0 and the filesize.
The chart plots the byte values of the binary file and let you focus only on the relevant sections. For example, if in a binary file there is an area full of null bytes, you can easily detect it from the chart.
LicenseGPL-3
Continue reading
- Pentest Tools Download
- Hacking Tools Name
- Hacker Hardware Tools
- Top Pentest Tools
- How To Hack
- Beginner Hacker Tools
- Hacking Tools 2020
- Hacking Tools For Windows Free Download
- Hacking App
- Hacking Tools Mac
- Hack Tools Online
- Hacker Tools Free Download
- Hacking Tools Windows 10
- Hack Tools Mac
- Hacker Tools Software
- Hacking Apps
- Pentest Tools Kali Linux
- Hacker Tools 2020
- Hacker Tools Linux
- Hacking Tools Online
- Pentest Tools For Ubuntu
- Hack Tools For Pc
- Hacker Tools For Pc
- Pentest Recon Tools
- Hacking Tools For Beginners
- Tools Used For Hacking
- Pentest Tools Tcp Port Scanner
- Hacker Tools Apk
- Pentest Tools Online
- Hacking Apps
- Hacker Tools List
- Pentest Tools
- Pentest Tools Online
- Hacking Tools Pc
- Hacking Tools For Windows Free Download
- Hacker Tools Free Download
- Pentest Tools Tcp Port Scanner
- Hacking Apps
- Hack Website Online Tool
- New Hacker Tools
- Pentest Tools Website
- Usb Pentest Tools
- Hacker Tools List
- Hackrf Tools
- Computer Hacker
- Hacking Tools And Software
- Hacker Hardware Tools
- Pentest Tools Website
- Hack Tools Mac
- Hacker Search Tools
- Hacker Security Tools
- Hack Rom Tools
- Hack Tool Apk No Root
- Hack Tools Pc
- Hacker Tools Free
- Pentest Tools For Android
- Nsa Hack Tools Download
- Physical Pentest Tools
- Usb Pentest Tools
- Pentest Tools For Ubuntu
- Hacking Tools
- Hacker Tools For Mac
- Hacker Security Tools
- Hacks And Tools
- Hacker Tools Linux
- Ethical Hacker Tools
- New Hacker Tools